“Legal functions will need to keep pace to ensure compliance with existing and new regulations….We will want to make sure our companies are using providers that know how to protect the storage of intellectual property and avoid potential infringement.”
On the heels of a global pandemic where safety requires that we socially distance and work from anywhere, demand is exploding for innovation to adapt to this new way of living. Our new environment will require more and more computing power to migrate to the edge of the network. Computing power housed in data centers and cloud environments is moving closer to end-users and devices in edge computing centers. Eventually, fueled by ubiquitous 5G+ connectivity bandwidths, one can foresee the migration of computing power to the very edge of your interconnected devices. Technology is racing forward to meet the challenges and exploit new opportunities. Ethical questions will need to be answered to regulate through the evolving network technology architecture. Corporate legal functions will need to adapt and partner with product managers to ensure compliance.
What is Edge Computing?
Edge computing can include any type of program that delivers low latency computing power at the closest point to the user and request. It’s computing power that happens outside of the cloud where real-time processing of data occurs. To distinguish edge computing from cloud computing, think of edge computing as computing power required to instantly analyze data generated by specific users and devices. In contrast, big data generated by masses of users and devices is analyzed in the cloud. Indeed, the two technologies work in tandem to form a network infrastructure or architecture.
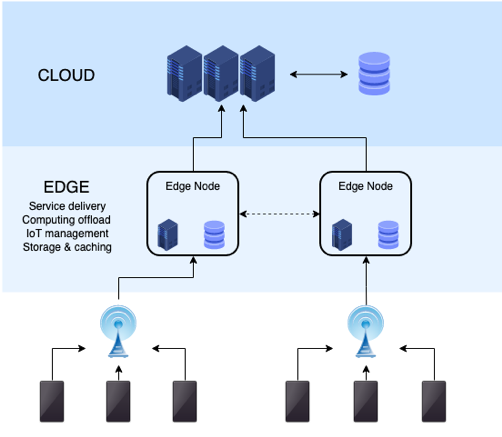
The following infogram illustrates the migration of data harvesting from the cloud, to “edge computing” nodes:
Source: By NoMore201 – Own work, CC BY-SA 4.0, https://commons.wikimedia.org/w/index.php?curid=82034067
With the rapid evolution of computing power, applications are being placed closer to data sources, such as local edge servers, and eventually, could move to the interconnected device itself. By moving computing power from public and private clouds to edge servers and nodes, edge computing can bring significant benefits, particularly when powered by 5G connectivity bandwidth. Edge computing’s closer proximity to sources of data should theoretically enable significant benefits, with faster speeds at lower latency, increased performance, virtualization due to faster computation, secure storage, content caching and Internet of Things (IoT) management, all with decreased bandwidth constraints.
Applications for Edge Computing
Powered by superfast 5G networks, artificial intelligence, quantum computing, cloud and edge servers, edge computing can enable the processing required to enable a greater number of increasingly complex IoT devices.
Some of the potential market applications for edge computing technology include automation, digital transformation, manufacturing, driverless or autonomous cars, augmented reality, gaming, sensors, data centers, wearables, smart cities and smart homes, improved clinical trials for pharmaceutical companies, digital health, telehealth and telemedicine, to name a few.
The Pandemic and Edge Computing
The migration of computing power from edge to edge has been accelerating for the past 20 years from your network to your hard-drive, then your laptop, smartphone, smartwatch, digital assistant and increasingly, to smart sensors placed strategically in your physical world.
Due to the global pandemic, travel has been significantly curtailed, if not rendered entirely unfeasible. There has been a massive shift in time previously spent primarily in an office, a school or in some form of mass transportation that is now spent in a single static “home” environment where we must live, eat, sleep, work, study and exercise. We can easily imagine a post-pandemic scenario where returning to the office does not occur, and we continue to “work from anywhere.”
The crisis has resulted not only in changed physical surroundings but also increased personal digital and bandwidth requirements amidst new biological safety imperatives requiring distance, masks, and clean air circulation. The convergence of these new physical, digital and biological worlds is rapidly changing the way we perceive, create, exchange, and distribute value. When Klaus Schwab theorized that a fourth industrial revolution would change the way we live and work, he might not have guessed that a global pandemic would expedite his paradigm-shifting futuristic vision to current reality.
With the outbreak focusing our attention on our individual spaces where we must both live and work, the demand for edge computing power is amplified. We require more capacity to analyze more sources of data from more users connecting more devices.
Distributing computer power to edge servers and edge computing technologies introduces new ethical, regulatory and legal issues and challenges.
Ethical and Regulatory Implications
As a result of the terabytes of new data being captured, regulatory frameworks must be created to address not only the data but also the burgeoning new information super-highways upon which it travels. Regulatory frameworks will reflect the ethical values of the societies and jurisdictions which adopt them.
As we have seen in the responses to the pandemic in certain countries, current western paradigms that prioritized personal liberties over societal good will be questioned, particularly when measured against non-western systems. Those regimes prioritized the inverse and benefited from lower infection and death rates while maintaining education systems, supply chains and quality of life.
Will 5G networks, cloud and edge computing centers be built with government surveillance keys? Will edge computing be used to track our movements? Will edge computing enable facial recognition to control our whereabouts and track our contacts? Will edge computing record our video and audio experiences? Will they be secure? Will everyone have equal access? How much energy will be required to power edge computing, and where will it come from?
To realize the full potential of edge computing and related technologies, we will need to build and maintain public trust and confidence by identifying and addressing the ethical questions—now.
The value judgments required to answer these ethical questions will surpass current regulatory paradigms. New governing frameworks will have to be adopted, and lawyers will need to work with engineers to design compliance into products, services and infrastructure.
Legal Implications
The infrastructure settings of edge computing solutions are crucial factors in information security and privacy, introducing a very complex scenario in terms of governance, risk and compliance. Legal functions will need to keep pace to ensure compliance with existing and new regulations:
Cyber-security. For companies with a distributed workforce, where we once adopted security procedures for handheld devices brought by employees to work, we will now need to adopt them for enterprise devices that employees bring home and anywhere. General data security training, with multiple security levels, restrictions on data transfer and network safety, will be more important than ever.
Third-party access. With distributed personnel at home and anywhere, the risk of unauthorized access by third parties to personal data exponentially increases. Workers will need to adopt methods of functioning that protect against malicious but also inadvertent third-party access to personal and private data.
Theft. Data can be compromised or breached wherever it is held. With the proliferation of edge computing nodes in the fog between the end user and the cloud, the security profile increases, with heightened vulnerability to so-called “man-in-the-middle” attacks. Traditional anomaly detection methods will not be sufficient. Encryption will need to be augmented. Disclosure policies in case of breach should be examined. Do our service level agreements contemplate all of this?
Intellectual property rights. When intellectual property is developed at home or anywhere (e.g., not in the office), the risk of confusion is amplified as to who owns that which is created. We will need to consider the rules and regulations of each jurisdiction where our employees are creating intellectual property. We will want to make sure our companies are using providers that know how to protect the storage of intellectual property and avoid potential infringement.
Data ownership. Customers’ data and information reside in the vendors infrastructures and servers that are dispersed, and new paradigms must be contemplated, adopted and regulated to ensure clear ownership of data.
Data integrity. As edge computing enables functions, responsibilities and management away from local ownership to third-party provided services, once the data is distributed and processed, how can the integrity of the data be guaranteed?
Deployment and maintenance. Who is responsible for deploying and maintaining these devices and networks where edge computing occurs, and who will repair defects? Once society determines who bears the burden, legal will enforce.
Digital health. Among edge computing’s primary beneficiaries has been the digital health market, which is leveraging massive new points of health data collected by connected sensors. The sensitivity of this shared healthcare data related to patients may increase the risks of privacy loss. Healthcare-related data will need more robust security measurements to prevent its disclosure and preserve patients’ privacy.
Energy consumption. While Moore’s Law and virtualization have decreased the amount of energy required to process a quantum of data, who will pay for the energy required to power edge computing?
Welcome to the Future
The pandemic is radically accelerating the pace of change in our society and the demand for technology solutions adapted for the times. New technology solutions are generating unprecedented amounts of data that is stored, processed and analyzed. New-use cases for how edge computing can be applied to target markets, particularly when used in combination with other emerging technologies and 5G bandwidth, abound.
The increasing number of these IoT environments powered by edge computing solutions will give rise to complex systems where data management triggers ethical dilemmas. Ethical questions about how we define our society will require answers and regulatory and legal tools to implement them.